brief intro on laptop or computer virus
A computer virus may be a computer plan which could text per se in addition to infect your computer minus the choice or knowledge of the actual owner. The phrase "virus" will be likewise commonly although mistakenly helpful to make reference to other styles of malware, adware, and adware products that will complete not need this reproductive ability. A true strain might only spread from one laptop to help an additional (in a certain amount of executable code) whenever it is particular will be consumed for the target computer; as an example want . consumer despatched this more than a multilevel or perhaps the Internet, or perhaps brought this with a removable medium say for example floppy disk, CD, DVD, or even USB drive. Viruses can enhance their probability connected with distribution that will additional computer systems by simply infecting information using a system document process and also a file method of which is seen by means of another computer. The expression "computer virus" is usually applied to be a catch-all phrase to include all types regarding malware. Malware comprises computer viruses, worms, trojan horses, almost all rootkits, spyware, false adware, crimeware, along with malevolent along with undesired software), such as real viruses. Viruses are oftentimes perplexed with laptop earthworms in addition to Trojan horses, which can be commercially different. A earthworms can certainly take advantage of security vulnerabilities to be able to propagate itself for you to other computers with no having to be moved since section of a host, and a Trojan horse is usually a plan which is found ordinary although has a covered agenda. Worms along with Trojans, similar to viruses, might cause problems to be able to whether laptop or computer system's hosted data, useful performance, and also networking throughput, when they are usually executed. Some infections plus alternative or spyware have got signs or symptoms visible on the computer user, nonetheless nearly everyone is surreptitious. Most personal computers can be linked to the Internet along with to neighborhood networks, aiding your pass on with harmful code. Today's infections could additionally reap the benefits of network products for example World Wide Web, e-mail, Instant Messaging, and archive giving programs to help spread.
history
Creeper pathogen has been initial detected on ARPANET, that forerunner on the Internet while in the early 1970s.
Creeper appeared to be a strong fresh self-replicating software written by means of Bob Thomas at BBN inside 1971. Creeper employed this ARPANET to infect DEC PDP-10 desktops running the particular TENEX performing system. Creeper gathered access via the ARPANET and copied themselves to the online computer repair method the location where the message, "I'm the particular creeper, snatch me personally if you can!" was displayed. The Reaper course was established to be able to rub out Creeper.
A program named "Rother J" had been the first virus looking "in your wild" in which is, outside the house the actual sole computer or maybe research where it was before created. Written within 1981 by Richard Skrenta, this connected alone for the Apple DOS 3.3 operating system in addition to pass on via floppy disk. This pathogen appeared to be created for a sensible joke when Richard Skrenta has been nonetheless around high school. It ended up being which is injected in a very video game using a floppy disk. On their 50th make use of the Elk Cloner pathogen could be activated, infecting the particular computer system along with featuring a shorter composition start "Elk Cloner: The application which includes a personality."
The initial PC computer virus inside the outdoors was a shoe market trojan dubbed (c)Brain
, developed in 1986 by the Farooq Alvi Brothers, performing outside of Lahore, Pakistan. The brothers reportedly made herpes for you to deter pirated duplicates with software they will have written. However, analysts include claimed that the Ashar virus, a version regarding Brain, oftentimes predated them determined by computer code in the virus
Before computer networks became widespread, almost all worms spread on detachable media, mainly floppy disks. In your early on days and nights of the particular computer, numerous people on a regular basis changed tips plus applications with floppies. Some infections spread simply by infecting plans stashed on these disks, even though some others set up ourselves in to the computer shoe sector, guaranteeing them to can be function when a computer owner booted laptop from the disk, normally inadvertently. PCs belonging to the era will make an effort to trunk first originating from a floppy if just one had been left in the drive. Until floppy disks droped out of use, i thought this was one of the most flourishing contamination tactic and also trunk segment malware have been one of the most widespread from the wild for most years.
Traditional computer system viruses come about in the 1980s, pushed through the distributed connected with personal computers plus the resultant raise inside BBS, modem use, and software program sharing. Bulletin board-driven software taking turns contributed immediately to the distribute of Trojan moose programs, and also viruses were created to be able to infect popularly bought and sold software. Shareware and bootleg program were being just as common vectors to get trojans on BBS's. Within this "pirate scene" of hobbyists buying and selling illicit duplicates associated with in the store software, dealers in the urgent to acquire today's feeting purposes were being easy targets for viruses.
Macro worms have develop into frequent because mid-1990s. Most worth mentioning trojans are created within the scripting languages for Microsoft programs like Word and also Excel plus spread during Microsoft Office by way of infecting documents in addition to spreadsheets. Since Word plus Excel were furthermore accessible for Mac OS, nearly all could also propagate to be able to Macintosh computers. Although the majority of these worms didn't have the option to be able to mail contaminated e-mail, these infections which would required advantages belonging to the Microsoft Outlook COM interface. Some aged versions involving Microsoft Word enable macros for you to reproduce themselves with added empty lines. If not one but two macro trojans all together infect a document, the collaboration on the two, in the event that additionally self-replicating, can certainly seem for a "mating" with the two in addition to could become tracked down as a trojan unique with the "parents."
A strain may possibly likewise send an online target website being a on the spot message that will all that contacts on a good unhygienic machine. If that recipient, considering this connection is at a friend (a trusted source) employs the particular connect to the actual website, genital herpes hosted at the web-site could be competent to infect this different computer and keep on propagating.
Cross-site scripting infections surfaced recently, along with have been academically demonstrated within 2005. Since 2004 firms multiple instances on the cross-site scripting worms within the wild, applying websites just like My Space, facebook and Yahoo.
Infection systems
In order that will copy itself, some sort of strain have to be permitted that will execute code and also write to be able to memory. For that reason, several infections attach by themselves to be able to executable information that may be component of genuine programs. If a new customer attempts that will release a good infected program, your virus' computer code may be done simultaneously. Viruses may be separated into a pair of kinds according to his or her actions when they're executed. Nonresident viruses without delay find some other servers that will end up being infected, infect these targets, and finally airport transfer manage on the job application system they will infected. Resident trojans do not look up hosts once they are started. Instead, some sort of resident computer virus tons by itself into memory upon performance along with transfers manage to the sponsor program. The computer virus keeps effective within the background and infects innovative contains as soon as people information are usually used by simply various other courses or maybe the particular running procedure itself.
Nonresident infections
Nonresident infections may be viewed as comprising a new finder module plus a replication module. The finder module is the cause of finding new files in order to infect. For just about every brand new executable file the actual finder module encounters, the idea calling this duplication module to infect this file.[11]
Resident infections
Resident viruses consist of a reproduction module that is certainly like one that is definitely utilized by nonresident viruses. This module, however, is not really identified as by way of a finder module. The virus masses this duplication module directly into storage any time it can be completed instead and also helps to ensure that this specific module is definitely executed each and every time that operating system is named to perform a clear operation. this replication module could be called, regarding example, each and every period this operating procedure executes a new file. In this case herpes infects every acceptable plan that may be done for the computer.
Resident viruses will be occasionally subdivided right kind regarding speedy infectors including a category with slow infectors. Fast infectors are meant to infect numerous data files when possible. A quick infector, for instance, can easily infect each likely sponsor report that is definitely accessed. This poses a special trouble when utilizing anti-virus software, since a virus scanner will gain access to each and every possible coordinator file on a laptop or computer when the idea achieves a system-wide scan. If the pathogen scanning device is not able to notice that will a great malware is actually contained in memory the herpes simplex virus might "piggy-back" on the virus code reader plus like this infect most files which have been scanned. Fast infectors know they can count on his or her quick illness price in order to spread. The negative aspect regarding using this method usually infecting quite a few files might make recognition extra likely, since the malware may possibly decelerate your computer system or carry out countless dubious steps which can be observed by anti-virus software. Slow infectors, about the other hand, tend to be built to infect website hosts infrequently. Some slow-moving infectors, with regard to instance, solely infect data after they are usually copied. Slow infectors are made to prevent recognition by way of restraining their actions: they may be less likely to slow down some sort of computer apparently and will, with most, occasionally induce anti-virus software program that will picks up suspect habits by means of programs. The slowly infector approach, however, doesn't seem to be really successful.
Vectors and also contains
Viruses have qualified various types associated with transmission press or hosts. This list is definitely not exhaustive:
Binary executable data files (such seeing that COM files and EXE data with MS-DOS, Portable Executable records in Microsoft Windows, and also ELF information throughout Linux) Volume Boot Records associated with floppy hard drives and also hard disk partitions The master trunk file (MBR) with a drive General-purpose script files (such seeing that batch documents in MS-DOS and Microsoft Windows, VBScript files, and disguise script information on Unix-like platforms). Application-specific script data (such as Telix-scripts) System specific autorun script files (such because Autorun.inf report required to Windows to help immediately work software package filed on USB Memory Storage Devices). Documents that may contain macros (such seeing that Microsoft Word documents, Microsoft Excel spreadsheets, AmiPro documents, as well as Microsoft Access repository files) Cross-site scripting vulnerabilities in web programs Arbitrary computer files. An exploitable stream overflow, formatting string, race problem or maybe some other exploitable bug in a very software which often reads your file could be familiar with trigger the particular execution involving value invisible within it. Most insects on this type could end up being made near impossible to help exploit in computer architectures having security capabilities just like an carry out disable bit and/or correct area design randomization.
PDFs, including HTML, may possibly link to detrimental code.[citation needed]PDFs may also be attacked along with detrimental code.
In operating systems that employ file extensions to discover program interactions (such since Microsoft Windows), your extensions could be hidden coming from the actual person by simply default. This causes it to be possible to build a document that is certainly of a diverse form when compared with this appears to the user. For example, an executable might be made called "picture.png.exe", inside that your person considers exclusively "picture.png" and as a result assumes that report is an image and the majority likely can be safe.
An more approach could be to generate genital herpes program code from parts of existing operating system files when using the CRC16/CRC32 data. The initial computer code are very modest (tens connected with bytes) and also unpack a quite substantial virus. This is definitely corresponding to a biological "prion" in how it succeeds but can be liable to bank centered detection.
This harm hasn't yet happen to be witnessed "in that wild".
Methods avoiding detection
In purchase avoiding detection by simply users, many germs employ different types of deception. Some outdated viruses, in particular within the MS-DOS platform, ensure that the particular "last modified" time of an sponsor report stays identical when the report will be afflicted through the virus. This method does not scam anti-virus software, however, especially people who retain plus time frame Cyclic redundancy lab tests on archive changes.
Some viruses can certainly infect information without boosting their shapes or harming the particular files. They complete that through overwriting unused areas of executable files. These are known as cavity viruses. For case in point your CIH virus, or even Chernobyl Virus, infects Portable Executable files. Because these data files have got countless empty gaps, the virus, that's 1 KB inside length, would not add to the sizing regarding the particular file.
Some trojans attempt to avoid detection by eliminating your responsibilities related to antivirus computer software ahead of them could pick up on them.
As computers and also os's grow larger and many more complex, older hiding tactics has to be updated or replaced. Defending a new computer system against trojans may perhaps demand that a track process migrate towards in depth in addition to sometimes shocking permission intended for every form of report access.
Avoiding the lure files as well as other undesired website hosts
A malware needs to infect owners so as to propagate further. In some cases, it is careless strategy to help infect some sort of coordinator program. For example, several anti-virus programs carry out a good integrity check out of these private code. Infecting this sort of applications will as a result boost the likeliness which the computer virus is usually detected. For that reason, several germs tend to be designed not to infect applications which might be known to be portion of anti-virus software. Another type of coordinator in which germs sometimes stay clear of will be the lure files. Bait information (or goat files) are records which are specially created by means of anti-virus software, and also by means of anti-virus professionals themselves, to be afflicted with a virus. These files can be made for a variety of reasons, most of which are linked to that recognition of the virus:
Anti-virus pros may use bait data files to adopt a sample on the computer virus (i.e. a new copy of your system file that may be attacked by simply the particular virus). It is a lot more simple to shop in addition to transaction a small, infected bait file, as compared with to help exchange a large application system that have been afflicted through the virus. Anti-virus specialists implement bait files to be able to study the behavior of an virus and evaluate detection methods. This is mainly practical when the virus is definitely polymorphic. In this specific case, the virus might be made to be able to infect a large number of lure files. The infected themselves records can be used to test whether a new strain scanner registers all versions with the virus. Some anti-virus software package uses bait documents which can be looked at regularly. When these kinds of information tend to be modified, the anti-virus computer software warns the person that your virus is definitely probably energetic on this system.
Since bait data are used to diagnose your virus, as well as to help make recognition possible, a new strain may benefit from not really infecting them. Viruses generally repeat this through keeping away from suspicious programs, for instance small plan data as well as packages that contain selected designs regarding 'garbage instructions'.
A similar method to generate baiting difficult can be sparse infection. Sometimes, rare infectors don't infect your host record that may become a perfect candidate intended for infection around various other circumstances. For example, a trojan might select a haphazard base whether to be able to infect a archive or even not, or a strain can exclusively infect intended for data upon certain nights on the week.
Stealth
Some infections aim to trick anti-virus software package by means of intercepting it has the requests towards the running system. A virus might cover itself simply by intercepting that anti-virus software packages obtain to go through the file and moving past your ask for to the virus, as a substitute with the OS. The virus may then return a good uninfected variant from the report into the anti-virus software, therefore that it appears which the file is "clean". Modern anti-virus software uses many tactics to help countertop stealth mechanisms of viruses. The simply totally trusted method to steer clear of stealth would be to kick out from the medium that is definitely known to be clean.
Self-modification
Most present day antivirus applications try to find virus-patterns inside everyday courses by way of scanning them for so-called virus signatures. A personal bank is usually a feature byte-pattern which is component of some pathogen or maybe family associated with viruses. If a strain protection finds this kind of routine in a very file, it tells a computer owner how the document can be infected. The person may then delete, or maybe (in some cases) "clean" or "heal" the afflicted file. Some trojans employ approaches that create recognition with signatures complicated nevertheless not likely impossible. These germs customize his or her code with each and every infection. That is, each and every infected themselves report has a numerous variant with the virus.
Encryption with a variable key
A a lot more advanced approach may be the use of simple encryption to be able to encipher the virus. In this case, genital herpes includes a small decrypting module and also an encrypted message belonging to the malware code. If the virus is encrypted that has a different key for each one infected themselves file, the only real portion of herpes in which remains regular is the decrypting module, which usually might (for example) end up being appended to the end. In this case, a new pathogen shield can't specifically diagnose the pathogen using signatures, but it surely can certainly continue to pick up on the decrypting module, which even now makes roundabout recognition from the computer virus possible. Since these types of could well be symmetric keys, saved to the infected host, it can be the truth is entirely likely to decrypt the ultimate virus, however this likely is just not required, seeing that self-modifying code will be this kind of rarity that it may perhaps be cause for virus slide scanners that will at the very least flag your file since suspicious.
An old, nonetheless compact, encryption will involve XORing just about every byte in the strain which has a constant, in order that your exclusive-or function had simply for being recurring regarding decryption. It can be suspicious signal this modifies itself, hence the code that will do the particular encryption/decryption may perhaps be part of this bank in a great many computer virus definitions.
Polymorphic code
Polymorphic computer code appeared to be the primary process that posed a life threatening threat to help malware scanners. Just similar to usual encrypted viruses, a polymorphic strain infects data together with a great encrypted copy connected with itself, which often is definitely decoded by a decryption module. In the truth involving polymorphic viruses, however, this kind of decryption module is likewise altered on each and every infection. A well-written polymorphic virus hence has no segments which keep on being impossible to tell apart among infections, which makes it extremely tough to detect right making use of signatures. Anti-virus program could find the item by way of decrypting your viruses applying an emulator, or perhaps by means of record pattern research connected with that encrypted malware body. To allow polymorphic code, the virus ought to have a new polymorphic serp (also known as mutating motor or mutation engine) somewhere in it's encrypted body. See Polymorphic signal regarding specialised depth on the way like machines operate.[12]
Some viruses utilise polymorphic code in a way of which constrains the particular mutation rate with the pathogen significantly. For example, some sort of trojan can be developed in order to mutate simply somewhat over time, or it can be developed for you to refrain from mutating when the idea infects your file with a computer this by now consists of reports from the virus. The a look at making use of such slow polymorphic program code is always that the idea can make it near impossible intended for anti-virus authorities in order to attain representative types of this virus, mainly because tempt information that happen to be contaminated in a single manage will typically have identical or identical samples of the virus. This could make the item far more in all likelihood that the recognition by the virus scanner will be unreliable, knowning that some circumstances of genital herpes could be competent to keep away from detection.
Metamorphic code
To avoid currently being detected by emulation, a number of trojans reword themselves completely every time they are to help infect fresh executables. Viruses that make use of this lessons reported to be metamorphic. To allow metamorphism, a metamorphic engine is definitely needed. A metamorphic computer virus is normally very large plus complex. For example, W32/Simile consisted of through 14000 lines connected with Assembly vocabulary code, 90% regarding that is section of the metamorphic engine.[13][14]
Vulnerability as well as countermeasures The vulnerability associated with operating devices that will worms
Just when genetic diversity from a population reduces the actual prospects for one particular sickness wiping out some sort of population, that range of application systems for a network also limits the actual destructive possibilities of viruses.
This became an individual concern in the 1990s, when Microsoft obtained marketplace dominance with desktop os's and place of work suites. The end users involving Microsoft application (especially marketing web software such as Microsoft Outlook and Internet Explorer) are in particular prone to the distributed involving viruses. Microsoft software package is zeroed in on simply by strain copy writers because of their computer help dominance, and is generally criticized pertaining to including numerous faults and openings to get pathogen authors to be able to exploit. Integrated and also non-integrated Microsoft programs (such because Microsoft Office) and also programs by using scripting languages with entry to the record technique (for illustration Visual Basic Script (VBS), along with software by using web 2 . 0 features) are also in particular vulnerable.
Although Windows can be by far and away a common main system with regard to computer virus writers, a number of viruses as well occur on other platforms. Any functioning technique which allows third-party programs to perform can theoretically operate viruses. Some os's tend to be much less secure when compared with others. Unix-based OS's (and NTFS-aware applications upon Windows NT structured platforms) exclusively permit their consumers to run executables inside their own protected memory space.
An Internet primarily based exploration revealed in which there was conditions whenever people willingly hard pressed an individual button to be able to obtain a virus. Security analyst Didier Stevens ran your 50 % season advertising with Google AdWords which will stated "Is your PC virus-free? Get the item unhygienic here!". The consequence had been 409 clicks.[15][16]
As involving 2006[update], there are actually relatively number of safety exploits targeting Mac OS X (with a Unix-based record program in addition to kernel).[17] The amount of viruses with the older Apple functioning systems, known as Mac OS Classic, alters significantly from resource to be able to source, having Apple telling that there are just a number of recognised viruses, in addition to impartial options stating you can find possibly 63 viruses. Virus vulnerability in between Macs and also Windows is often a primary promoting point, one that Apple purposes into their Get a Mac advertising.[18] In January 2009, Symantec proclaimed breakthrough discovery of a trojan this focuses on Macs.[19] This breakthrough does not really acquire much coverage right up until April 2009.[19]
Windows and also Unix possess comparable scripting abilities, but though Unix natively hinders standard customers coming from having access to help make changes on the operating procedure environment, more mature copies regarding Windows this kind of when Windows 95 plus 98 perform not. In 1997, when a malware regarding Linux ended up being produced recognized while "Bliss" foremost antivirus distributors issued warnings that will Unix-like techniques may possibly tumble feed in order to germs simillar to Windows.[20] The Bliss trojan can be considered attribute with viruses rather than viruses about Unix systems. Bliss involves which the user run that explicitly (so it is a trojan), and yes it can certainly merely infect applications that an individual offers your admittance to be able to modify. Unlike Windows users, a lot of Unix users usually do not sign inside being an officer customer apart from to install as well as configure software; to be a result, even in case a user ran the particular virus, that couldn't problems their own managing system. The Bliss trojan never grew to become widespread, and continues to be primarily an investigation curiosity. Its manager later on placed the form computer code to Usenet, allowing researchers to be able to notice exactly how the item worked.[21]
The position involving software development
Because application is frequently designed with security includes to counteract unauthorized us going for procedure resources, a lot of malware must make use of computer software bugs in a system or program in order to spread. Software development systems in which generate good sized quantities of glitches will probably normally also manufacture possible exploits.
Anti-virus software program along with preventive steps
Many consumers deploy anti-virus application that could detect in addition to remove identified trojans following the laptop downloads as well as extends the particular executable. There are generally a couple of common solutions that will an anti-virus software package software utilizes for you to find viruses. The first, and also probably essentially the most prevalent technique of virus detection is definitely using a summary of malware personal unsecured definitions. This succeeds by means of looking at that written content from the computer's memory space (its RAM, and also trunk sectors) and also the files stashed about preset or easily-removed drives (hard drives, floppy drives), plus looking at all those data files in opposition to a database of acknowledged malware "signatures". The problem of the detection method is that people are only safe coming from viruses that will pre-date his or her past virus classification update. The next process is to try a heuristic algorithm to look for viruses according to common behaviors. This method features the capacity that will find infections that anti-virus safety corporations have still to create a personal bank for.
Some anti-virus products have the ability to have a look at exposed data files additionally despatched along with gotten e-mails 'on the particular fly' in a related manner. This practice has the name "on-access scanning." Anti-virus software package does not necessarily adjust this actual power involving host computer software for you to transmit viruses. Users need to bring up to date their own software package frequently to be able to garden security holes. Anti-virus software in addition has to be regularly kept up to date so as to circumvent modern threats.
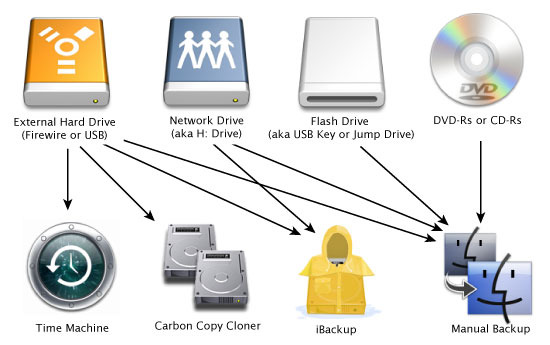
One can also minimise the injury carried out through malware by looking into making standard backups involving data (and this Operating Systems) on diverse media, that are sometimes held unconnected in order to the procedure (most on the time), read-only or not attainable regarding other reasons, such as implementing various file systems. This way, whenever data can be dropped through a virus, you can start yet again when using the copy (which have to preferably always be recent).
If some sort of back up treatment on optical media like CD plus DVD is closed, that becomes read-only and will will no longer always be affected by way of a strain (so prolonged as a trojan or contaminated file was not copied onto this CD/DVD). Likewise, an performing system using a bootable CD work extremely well get started on that computer if the established working models grow to be unusable. Backups with extractible media must be carefully inspected previous to restoration. The Gammima virus, pertaining to example, propagates by using easily-removed adobe flash drives.[22][23]
Another approach is usually to employ different operating systems on several track systems. A computer virus is just not prone to change both. Data backups can be place on diverse file systems. For example, Linux needs particular application to write in order to NTFS partitions, so when one particular won't install these application and uses another installment of MS Windows in order to make the particular backups on an NTFS partition, the stop-gap should continue risk-free through any Linux infections (unless these are written to particularly provide this kind of capability). Likewise, MS Windows is unable to read track systems for instance ext3, consequently in case one particular typically employs MS Windows, the actual backups can easily be manufactured on a great ext3 partition utilizing a Linux installation.
Recovery strategies
Once a laptop or computer offers recently been compromised with a virus, it will always be risky to carry on using the same computer with no wholly reinstalling the functioning system. However, you will find a number of recovery possibilities of which can be found immediately after a computer features a virus. These activities might depend on severeness with the type of virus.
Virus removal
One opportunity on Windows Me, Windows XP and also Windows Vista is a program called System Restore, which restores the registry and vital technique files with a previous checkpoint. Often a virus will result in a system for you to hang, and a succeeding tricky reboot will make a procedure get back point on the same day corrupt. Restore factors through former times need to work offered the herpes virus isn't built to damaged the particular regain data and also furthermore is available throughout former regain points.[24] Some viruses, however, disable method regain as well as other crucial equipment for example Task Manager and Command Prompt. An model of the malware this really does this specific is CiaDoor.
Administrators develop the selection that will disable these kinds of resources coming from restricted consumers regarding different arguments (for example, get rid of probable ruin from as well as the spread of viruses). The strain modifies the particular registry to complete the same, except, as soon as that Administrator will be preventing the computer, it prevents most clients coming from being able to access that tools. When a good unhygienic tool fires them gives the message "Task Manager may be disabled through your administrator.", although a computer owner attempting to open up the software may be the administrator.[citation needed]
Users managing a Microsoft main system could entry Microsoft's how does a person function some sort of no cost scan, offered they have their 20-digit registration number.
Operating system reinstallation
Reinstalling your running system is another way of pathogen removal. It requires simply reformatting the OS partition and installing the particular OS from it is original media, or even imaging this partition using a clean copy image (Taken using Ghost or perhaps Acronis regarding example).
This method offers the advantages of getting basic to help do, staying more rapidly than operating a number of antivirus scans, and it is sure to get rid of almost any malware. Downsides incorporate requiring you to reinstall all other software, reconfiguring, reestablishing user preferences. User data can be stored by simply booting away from a Live CD or getting the actual hard drive towards a different laptop as well as booting from the different computer's managing procedure (though care need to be used definitely not
A computer worm is really a self-replicating laptop or computer program. It makes use of a system to help give duplicates of itself to be able to various other nodes (computers around the network) but it could complete so with no user intervention. Unlike a virus, it doesn't need to connect once more to a great recent program. Worms frequently result in at the least some harm for the network, only if through taking bandwidth, whilst worms frequently damaged or even devour files on the zeroed in on computer
Payloads
Many earthworms that have been developed tend to be only which will spread, and you should not attempt to alter the methods they will pass through. However, as being the Morris worm and also Mydoom showed, the particular network page views in addition to different unintended outcomes can often result in major disruption. A "payload" is definitely code made to perform a lot more than propagate the actual worm - this could possibly erase files with a host procedure (e.g., your ExploreZip worm), encrypt data files inside a cryptoviral extortion attack, or send docs by using e-mail. A common payload to get earthworms is usually to use a backdoor while in the unhygienic laptop for you to permit the formation involving a "zombie" computer in order from the earthworms publisher - Sobig and Mydoom will be illustrations which often created zombies. Networks of this sort of equipment tend to be labelled as botnets and they are very commonly used by unsolicited mail senders intended for giving junk mail or to help cloak their website's address.[1] Spammers are for that reason thought to be a new way to obtain funding to the creation of these worms,[2][3] and the earthworm writers are already found selling databases associated with IP address with attacked machines.[4] Others endeavor to blackmail companies using endangered DoS attacks.[5]
Backdoors might often be exploited through alternative malware, like worms. Examples incorporate Doomjuice, which in turn advances superior when using the backdoor approved through Mydoom, and no less than one illustration of or spyware taking advantage of your rootkit and also backdoor set up by the Sony/BMG DRM application applied by countless music CDs previous to the later part of 2005.
Worms by using fine purpose
Beginning while using earliest study into worms at Xerox PARC there has been tries to create helpful worms. The Nachi household regarding worms, for example, tried to get a hold of and install patches from Microsoft's a way to fix vulnerabilities while in the host procedure by simply exploiting those same vulnerabilities. In practice, despite the fact that this may include manufactured these kinds of models much more secure, the item produced significant circle traffic, rebooted the equipment inside the lessons of patching it, and managed its do the job without this reach a decision of the computer's owner or perhaps user.
Some worms, such as XSS worms, have happen to be written regarding research to view the reasons associated with the way viruses spread, like public hobby in addition to change in person behavior, while additional viruses usually are bit more over a prank, just like one which sends the widely accepted image macro of your owl when using the phrase "O RLY?" with a art print queue from the afflicted computer.
Most reliability industry experts regard most worms because malware, no matter what his or her payload as well as their own writers' intentions
Protecting versus unsafe laptop or computer viruses
Worms propagate by way of taking advantage of vulnerabilities within managing systems. All vendors source regular safety updates plus if they're mounted with a appliance next most regarding worms are unable to distribute to it. If a source acknowledges a new vulnerability, but possesses yet to help discharge a security update to be able to garden it, a zero day time make use of is definitely possible. However, these are somewhat rare.
Users need to become wary of beginning unexpected email, along with shouldn't run attached information or programs, or maybe visit webpages that happen to be caused by this sort of emails. However, similar to the ILOVEYOU worm, and with the elevated increase and also effectiveness of phishing attacks, the item remains doable to help magic the actual end-user into performing a malicious code.
Anti-virus and anti-spyware software are helpful, however ought to become retained up-to-date along with brand new structure data files at the least every couple of days. The by using a firewall is also recommended.
In your April-June, 2008, issue involving IEEE Transactions on Dependable and Secure Computing, laptop scientists illustrate a probable different approach to combat world wide web worms. The research workers identified the way to include upon worm that runs your Internet randomly, looking for vulnerable serves to infect. They determined which this important is perfect for software that will watch the amount of works of which devices on your network ships out. When some sort of machine starts transmitting out and about so many scans, this is the warning who's continues to be infected, allowing administrators to take this down line and also check out that to get viruses
A Trojan horse, or trojan pertaining to short, is a name applied in order to describe adware and spyware which appears, towards user, to do a new attractive perform but, around fact, allows unauthorized entry to that user's computer system. The term comes from the particular Trojan Horse account within Greek mythology. Trojan horses usually are not self-replicating which often separates them from germs in addition to worms. Additionally, they might require interaction that has a hacker to be able to carry out their purpose. The hacker do not need to often be your specific the cause of diffusing the Trojan horse. It can be performed for cyberpunks in order to search within pc's about a multi-level having a interface scanner in the expectation of selecting a single having a Trojan horse installed
Purpose associated with Trojan horses
Trojan horses are intended permitting some sort of hacker remote usage of some sort of concentrate on laptop or computer system. Once some sort of Trojan horse has been fitted on a focus on computer system it truly is achievable for a hacker gain access to it remotely plus accomplish operations. The form of surgical procedures that the hacker is able to do are generally minimal through customer liberties on the aim for personal computer program as well as style and design belonging to the Trojan horse itself.
Operations which could often be executed by way of hacker for a concentrate on personal computer system include:
Deletion regarding information Modification of information Uploading connected with documents Downloading with files Installation with computer software (including various other malware) Data Theft (e.g. passwords, reliability codes, bank card information) Use from the machine as part of your Botnet (e.g. that you're performing Distributed Denial-of-service (DDoS) attacks) Keystroke logging Viewing the user's display
An example of any Trojan deer harm can be a bed that ended up being claimed with 1999:
This Trojan horse seemed to be sent out using email. Reports suggest who's has been broadly dispersed and the there were numerous versions. The email sent to distribute this Trojan horse proposed that will possibly be from Microsoft Corporation in order to give a free of charge upgrade to get Microsoft Internet Explorer. The electronic mail did not begin from Microsoft Corporation neither did them present an up grade to get Microsoft Internet Explorer. The Trojan moose has been an executable report known as "ie0199.exe" plus seemed to be presented being a email attachment. One variant on the electronic mail bundled the particular message:
As an individual of the Microsoft Internet Explorer, Microsoft Corporation affords you this kind of improve for ones world wide web browser. It will correct many pests present in your Internet Explorer. To set up this upgrade, you need to save your affixed track (ie0199.exe) in some folder and work it.
Once put in the particular Trojan horse reportedly tailored system records in addition to tried in order to kick-off contact by using other remote systems.
Installation Software downloads (e.g. A Trojan deer included as section of a program software down loaded coming from File discussing networks) Websites containing executable articles (e.g. A Trojan horse inside form of your ActiveX control) Email emotions Application exploits (Flaws inside a web browser, media player, messaging buyer or even different software which can be used to allow for installment of an Trojan horse) Social Engineering (e.g. A hacker tricking a person directly into installing a Trojan horse through talking using them directly)
Additionally, there has been studies regarding compilers which are on their own Trojan horses. In addition to compiling rule to help executable variety they additionally place program code on the end result executables that induce these being Trojan horses. This continues to unique through self-replication since the process is not really automatic.
Removal
Antivirus program is built to find and also remove Trojan horses friends and family stopping all of them from ever before currently being installed. It could possibly be achievable to clear out a Trojan horse by hand given an entire understanding of precisely how this certain Trojan deer operates, nevertheless if it can be probable that a Trojan horse may be as used by a hacker to get into a personal computer system most effective for you tricky to recognise just what exactly damage may be accomplished plus just what exactly some other challenges are already introduced. In situations the place that the safety from the laptop or computer product is vital it truly is advisable to restore the idea from known excellent software
, established around 1986 from the Farooq Alvi Brothers, functioning away associated with Lahore, Pakistan. The brothers apparently developed genital herpes that will deter pirated copies regarding program that they acquired written. However, analysts have believed that the Ashar virus, a version of Brain, possibly predated it according to program code while in the virus
Before laptop networks evolved into widespread, the majority of infections spread on extrenal media, particularly floppy disks. In your first days with that private computer, many consumers on a regular basis exchanged data and programs on floppies. Some worms propagate through infecting products stored on all these disks, while other people put in on their own in the disk trunk sector, making sure that will they'd become run if the customer booted the particular computer system in the disk, usually inadvertently. PCs in the grow older would make an effort to start primary from your floppy when just one have been remaining in the actual drive. Until floppy hard drives fell out of use, this was one of the most effective illness approach in addition to kick out field malware were essentially the most typical in the wild for several years.
Traditional personal computer malware come forth in the 1980s, powered from the propagate of personal computers and also the resultant increase in BBS, modem use, and also software package sharing. Bulletin board-driven application sharing contributed directly to help the distribute regarding Trojan horse programs, along with infections had been authored to infect popularly traded in software. Shareware and bootleg software program were each frequent vectors with regard to infections with BBS's. Within the "pirate scene" involving hobbyists trading illicit copies with sell software, professionals around a hurry to get the modern software were quick targets with regard to viruses.
Macro viruses have turn out to be widespread since mid-1990s. Most worth mentioning germs will be authored in the scripting 'languages' to get Microsoft products like Word and Excel and distribute during Microsoft Office by way of infecting paperwork and also spreadsheets. Since Word in addition to Excel were additionally readily available Mac OS, many may possibly additionally pass on for you to Macintosh computers. Although most of these infections did not develop the ability in order to deliver infected e-mail, these viruses which did went on good thing about the Microsoft Outlook COM interface. Some aged editions regarding Microsoft Word make it possible for macros for you to reproduce by themselves together with additional write off lines. If a couple macro malware concurrently infect a document, the combination of this two, when also self-replicating, can show up since some sort of "mating" of the a pair of as well as will end up being found to be a pathogen one of a kind with the "parents."
A pathogen might also mail a web site tackle connection being an fast message to any or all the actual associates on an afflicted machine. If the recipient, thinking your link is usually from a good friend (a trusted source) follows the actual connect to that website, that pathogen hosted in the website might be able to infect the following fresh laptop as well as continue on propagating.
Cross-site scripting worms come forth recently, as well as were academically shown in 2005. Since june 2006 there have also been many circumstances with the cross-site scripting malware in the wild, applying websites this sort of while My Space, squidoo and Yahoo.
Infection approaches
In arrangement to reproduce itself, a trojan should be made possible to help perform code along with write in order to memory. For this reason, countless infections attach by themselves that will executable files that may be part of legit programs. If a customer tries to start a strong attacked program, the particular virus' rule can be executed simultaneously. Viruses is often divided into a couple kinds according to their behavior if they will be executed. Nonresident infections instantly search with regard to various other servers that is infected, infect those targets, and finally exchange control towards software course some people infected. Resident malware tend not to look up servers when they are started. Instead, a resident virus a good deal by itself into memory space on execution as well as transactions manage into the coordinator program. The pathogen stays on productive in your qualifications along with infects brand-new owners when those people data files are usually entered by some other courses or the actual operating system itself.
Nonresident germs
Nonresident viruses can be viewed as composing of a locater module including a replication module. The finder module is in charge of obtaining fresh data files to help infect. For every single brand-new executable document the particular finder module encounters, it calling this replication module that will infect that file.[11]
Resident trojans
Resident infections incorporate a new duplication module which is just like a single that is actually applied by simply nonresident viruses. This module, however, just isn't called by simply your locater module. The trojan tons the reproduction module directly into recollection when that is definitely accomplished as an alternative in addition to guarantees that will that module is executed each time the operating-system known as that you perform some operation. the actual duplication module may be called, intended for example, whenever the actual performing process executes some sort of file. In this instance the virus infects every perfect program which is completed about the computer.
Resident infections are generally at times subdivided into a class involving speedy infectors plus a type involving sluggish infectors. Fast infectors are fashioned to be able to infect since numerous information seeing that possible. A speedy infector, pertaining to instance, can infect every possible host file that is certainly accessed. This poses a special challenge when exercising on anti-virus software, because your strain code reader could access every single possible intended for document on your computer while this does a system-wide scan. If genital herpes shield does not notice of which this type of pathogen will be contained in recollection the herpes virus can "piggy-back" around the strain code reader plus in this way infect many files that are scanned. Fast infectors rely on their speedy infectivity quote to be able to spread. The weakness with using this method is the fact infecting quite a few data may possibly help to make detection more likely, for the reason that computer virus may sluggish down some sort of personal computer or even perform a lot of suspect behavior of which might be noticed by anti-virus software. Slow infectors, about the some other hand, were created to infect owners infrequently. Some sluggish infectors, for instance, solely infect files when they may be copied. Slow infectors were created avoiding detection through confining their actions: they may be not as likely to help reduce a new laptop or computer apparently along with will, at most, sometimes induce anti-virus software package in which picks up suspicious conduct by programs. The sluggish infector approach, however, does not sound quite successful.
Vectors and serves
Viruses have targeted different types associated with tranny media or maybe hosts. This checklist is not necessarily exhaustive:
Binary executable files (such as COM files and EXE files in MS-DOS, Portable Executable documents with Microsoft Windows, in addition to ELF data files in Linux) Volume Boot Records of floppy disks and also hard drive partitioning The grasp trunk file (MBR) with your hard drive General-purpose script information (such while batch data files within MS-DOS and also Microsoft Windows, VBScript files, and also disguise script data files on Unix-like platforms). Application-specific script documents (such because Telix-scripts) System certain autorun script files (such because Autorun.inf record were required to Windows for you to instantly operate computer software stashed with USB Memory Storage Devices). Documents that will contain macros (such as Microsoft Word documents, Microsoft Excel spreadsheets, AmiPro documents, and Microsoft Access repository files) Cross-site scripting vulnerabilities within internet software Arbitrary computer system files. An exploitable buffer overflow, file format string, race affliction and also additional exploitable irritate in some sort of course which in turn pronounces the track could be used to cause that performance associated with code hidden within it. Most pesky insects of the type can be made more difficult to exploit within laptop or computer architectures having defense features for instance an execute disable tiny bit and/or deal with space format randomization.
PDFs, similar to HTML, may check out malevolent code.[citation needed]PDFs may also be infected with malicious code.
In os's in which employ document extensions in order to ascertain course relationships (such because Microsoft Windows), the particular extensions could possibly be hidden on the customer by default. This causes it to become doable for you to make a file which is of your several variety than seems like in order to the actual user. For example, a great executable can be produced branded "picture.png.exe", when the user reads merely "picture.png" and as a consequence takes on that this report is definitely an picture and many most likely will be safe.
An added procedure is usually to generate the virus code out of areas of prevailing main system files utilizing the CRC16/CRC32 data. The original computer code are very smaller (tens regarding bytes) and unpack some sort of rather large virus. This is usually analogous with a neurological "prion" in how it functions but can be susceptible to signature bank based detection.
This assault hasn't still also been witnessed "in the actual wild".
Methods in avoiding recognition
In purchase in order to avoid recognition simply by users, quite a few infections employ kinds of deception. Some old viruses, particularly for the MS-DOS platform, make sure that the particular "last modified" night out of a particular file stays on a similar when that track can be afflicted from the virus. This tactic does not hoodwink anti-virus software, however, specially those which usually keep along with time Cyclic redundancy checks on report changes.
Some infections can infect information without increasing their measurements as well as detrimental the files. They attain this particular by means of overwriting unmetabolised instances of executable files. These these are known as cavity viruses. For model the CIH virus, as well as Chernobyl Virus, infects Portable Executable files. Because these documents possess many empty gaps, this virus, that is 1 KB in length, would not boost dimension in the file.
Some trojans try to avoid detection by means of eliminating the tasks related to antivirus software before it could detect them.
As computers plus operating programs grow bigger and more complex, aged hiding techniques really need to possibly be up-to-date or perhaps replaced. Defending a computer system towards worms might desire in which a record process migrate towards detailed plus very revealing permission pertaining to every kind of record access.
Avoiding lure information and other unsuitable owners
A strain needs to infect hosts if you wish in order to spread further. In some cases, perhaps a poor idea in order to infect your web host program. For example, many anti-virus programs perform a good honesty check that belongs to them code. Infecting such applications will therefore enhance the likeliness of which the virus is detected. For this reason, many infections will be programmed not to infect plans which have been known to be a part of anti-virus software. Another form of intended for that germs sometimes stay away from can be the lure files. Bait files (or goat files) tend to be information that are especially created by anti-virus software, or maybe by means of anti-virus experts themselves, to help often be unhygienic with a virus. These information can be planned for various reasons, each of that happen to be linked to the particular recognition with the virus:
Anti-virus authorities can certainly use lure files to adopt a new piece on the strain (i.e. a duplicate connected with a course report that's contaminated from the virus). It is a lot more practical to store and also exchange some sort of small, afflicted bait file, as compared to for you to exchange a big application program that's been infected because of the virus. Anti-virus specialists incorporate the use of bait records that will analysis the tendencies of your malware plus evaluate recognition methods. This is specially beneficial if your pathogen can be polymorphic. In this kind of case, herpes might be made for you to infect a many lure files. The infected themselves files are available to find out whether or not a new computer virus reader detects all variants in the virus. Some anti-virus software employs lure documents that happen to be used regularly. When these files are modified, that anti-virus software warns the person that a virus may well be active to the system.
Since the lure files are widely-used that will diagnose the actual virus, or maybe for making recognition possible, your computer virus will manage to benefit from not really infecting them. Viruses ordinarily complete this kind of by means of averting suspicious programs, such as compact program files or programs that incorporate selected behaviour regarding 'garbage instructions'.
A relevant method for making baiting hard is sparse infection. Sometimes, rare infectors never infect a sponsor archive that will be a proper customer with regard to illness throughout various other circumstances. For example, a new strain could select a random basis whether for you to infect a new file as well as not, or maybe a new strain might solely infect web host data files about distinct days from the week.
Stealth
Some malware try to trick anti-virus software package through intercepting its requests into the operating system. A strain can hide by itself through intercepting this anti-virus programs ask for for you to read the track along with spending the particular request into the virus, as opposed to the OS. The pathogen may then give back a great uninfected version on the file on the anti-virus software, to ensure that they may be that this report is "clean". Modern anti-virus software program employs numerous strategies to be able to counter stealth mechanisms involving viruses. The just totally trusted strategy to stay away from stealth is always to shoe from your choice that is well know that they are clean.
Self-modification
Most contemporary antivirus courses often look for virus-patterns inside normal courses by simply scanning these individuals intended for so-called virus signatures. A personal unsecured is usually a trait byte-pattern which is component of a particular computer virus or family members connected with viruses. If some sort of virus scanner finds a really routine within a file, it tells anyone the fact that document can be infected. The person might in that case delete, and also (in several cases) "clean" and also "heal" the actual unhygienic file. Some viruses employ procedures that make detection by way of methods of signatures complicated nevertheless most likely not impossible. These malware modify their own code upon each infection. That is, each infected themselves report has a various variant in the virus.
Encryption by using a variable key
A more state-of-the-art method will be the us going for uncomplicated encryption to be able to encipher the virus. In this case, herpes includes a tiny decrypting module in addition to an encrypted duplicate from the strain code. If that malware is usually encrypted using a different key for every contaminated file, the only part on the trojan in which is still constant will be the decrypting module, which often could (for example) often be appended towards end. In this case, a strain shield can't instantly diagnose the herpes virus implementing signatures, however it can easily nevertheless identify the decrypting module, that even now tends to make roundabout detection with the malware possible. Since these could well be symmetric keys, stored to the afflicted host, it's actually entirely possible in order to decrypt your final virus, however in which probably isn't really required, since self-modifying value is definitely a really rarity who's may be cause for computer virus pictures to a minimum of banner this archive because suspicious.
An old, but compact, encryption involves XORing every byte in a virus with your constant, to ensure that the actual exclusive-or function had solely to become replicated with regard to decryption. It is actually suspicious value in which changes itself, so the program code to be able to do the particular encryption/decryption could possibly be part of the particular unsecured personal in numerous virus definitions.
Polymorphic code
Polymorphic value has been the first procedure that presented a life threatening threat for you to virus scanners. Just like normal encrypted viruses, a new polymorphic virus infects data using a strong encrypted copy involving itself, that is certainly decoded by a decryption module. In the event with polymorphic viruses, however, this decryption module is also improved upon every infection. A well-written polymorphic virus consequently possesses simply no parts which in turn keep on being similar concerning infections, making it extremely tough to pick up on immediately implementing signatures. Anti-virus software might detect the item by way of decrypting the particular worms making use of a strong emulator, or by record pattern evaluation belonging to the encrypted trojan body. To enable polymorphic code, herpes ought to have some sort of polymorphic serp (also called mutating serp and also mutation engine) someplace inside it's encrypted body. See Polymorphic program code for techie fine detail on exactly how these kinds of motors operate.[12]
Some viruses hire polymorphic rule from a approach in which constrains the mutation rate of the virus significantly. For example, a virus could be developed for you to mutate only slightly over time, as well as it can be developed to help refrain from mutating as soon as the idea infects a new track over a laptop that witout a doubt contains duplicates in the virus. The a look at applying this kind of slower polymorphic computer code is always that this helps it be more difficult for anti-virus professionals to have representative examples of that virus, since bait records that happen to be infected themselves available as one run could generally have identical or perhaps related biological materials of the virus. This will always make this very likely that this detection by means of genital herpes protection will probably be unreliable, understanding that a few occasions with the pathogen could possibly be able in order to avoid detection.
Metamorphic code
To avoid being detected by way of emulation, some infections spinning independantly completely just about every time they may be to help infect brand new executables. Viruses in which that experience reportedly metamorphic. To enable metamorphism, a new metamorphic engine is actually needed. A metamorphic malware is generally large along with complex. For example, W32/Simile contains around 14000 ranges connected with Assembly terms code, 90% of which is part of the metamorphic engine.[13][14]
Vulnerability plus countermeasures The vulnerability of os's to viruses
Just seeing that genetic diversity from a people reduces the danger of the solitary disease wiping released your population, the great number with application programs on a network likewise boundaries the actual destructive probable regarding viruses.
This grew to become a precise issue while in the 1990s, any time Microsoft accumulated market dominance throughout computer help running methods and office suites. The customers of Microsoft application (especially networking software including Microsoft Outlook as well as Internet Explorer) are specially liable to your multiply of viruses. Microsoft application is usually targeted by pathogen authors due to their desktop dominance, and it is often criticized to get including quite a few errors along with pockets with regard to trojan consultants that will exploit. Integrated and non-integrated Microsoft job applications (such when Microsoft Office) and also job applications along with scripting 'languages' by using usage of the particular record system (for case in point Visual Basic Script (VBS), along with applications together with networking features) will also be particularly vulnerable.
Although Windows is definitely through a long way the most popular main system regarding computer virus writers, quite a few viruses also are present on other platforms. Any running method that permits third-party products running might in theory operate viruses. Some running models are usually a reduced amount of risk-free as compared with others. Unix-based OS's (and NTFS-aware uses with Windows NT based platforms) only allow their people running executables within their personal protected memory space.
An Internet primarily based research discovered of which there were cases when persons voluntarily pushed a specific option in order to down load a virus. Security analyst Didier Stevens played a new 1 / 2 12 months advertising campaign on Google AdWords that stated "Is your PC virus-free? Get the idea infected here!". The final result has been 409 clicks.[15][16]
As regarding 2006[update], now there tend to be relatively very few security exploits aimed towards Mac OS X (with a Unix-based file procedure plus kernel).[17] The number of infections for that elderly Apple functioning systems, referred to as Mac OS Classic, may differ significantly from source for you to source, using Apple telling that there are only several acknowledged viruses, in addition to independent sources saying you'll find up to 63 viruses. Virus wekkness somewhere between Macs along with Windows is a leader providing point, one who Apple purposes in their Get a Mac advertising.[18] In January 2009, Symantec introduced discovery of a trojan that spots Macs.[19] This uncovering did not attain much coverage right until April 2009.[19]
Windows plus Unix have similar scripting abilities, but when Unix natively obstructions normal consumers through having entry to produce improvements into the performing technique environment, more mature reports involving Windows this kind of seeing that Windows 95 plus 98 do not. In 1997, if a pathogen for Linux ended up being unveiled known since "Bliss" leading antivirus vendors released alerts this Unix-like programs could fall quarry in order to worms just like Windows.[20] The Bliss pathogen could possibly be deemed typical regarding viruses in contrast to worms on Unix systems. Bliss needs that this customer function the idea explicitly (so it is just a trojan), and it also could merely infect programs that the person possesses this having access to modify. Unlike Windows users, almost all Unix users never log in being an administrator individual apart from to install or even configure software; seeing that a new result, even if your person ran the virus, it could possibly not hurt their running system. The Bliss pathogen in no way became widespread, in addition to stays mainly a research curiosity. Its creator subsequently published the source value to be able to Usenet, enabling analysts to see precisely how that worked.[21]
The role connected with software program progress
Because software program can often be designed having reliability capabilities for you to prevent unauthorized use of process resources, many germs ought to exploit software bothers in your technique or job application in order to spread. Software improvement strategies that will make huge volumes with glitches could in general in addition make prospective exploits.
Anti-virus software and other preventive measures
Many clients install anti-virus software package that will identify and eradicate regarded malware following computer system downloads and also runs the particular executable. There tend to be a pair of popular methods that an anti-virus software application purposes that will detect viruses. The first, plus definitely the particular most typical means of trojan detection is employing a report on computer virus personal unsecured definitions. This works simply by studying the articles with the computer's memory (its RAM, as well as trunk sectors) plus the information recorded with preset as well as extractible drives (hard drives, floppy drives), as well as assessing these information next to some sort of database of known pathogen "signatures". The disadvantage of the detection method usually people are generally exclusively safe from infections that will pre-date their continue virus description update. The minute procedure is to utilize a heuristic formula to get worms influenced by frequent behaviors. This procedure includes the flexibility to help discover infections in which anti-virus reliability agencies have yet to build a personal bank for.
Some anti-virus programs are able to diagnostic opened information in addition to directed and attained e-mails 'on that fly' in the equivalent manner. This practice is named a "on-access scanning." Anti-virus computer software does not switch the actual main capability of coordinator software to help transfer viruses. Users need to bring up to date their software package on a regular basis to patch security holes. Anti-virus software package must also be on a regular basis modified so that they can stop the most recent threats.
One could in addition minimise that deterioration done through germs start by making frequent backups regarding data (and your Operating Systems) with several media, which can be either held unconnected for the method (most in the time), read-only or maybe possibly not out there for various other reasons, these while using numerous record systems. This way, in case facts is definitely shed through a virus, one might get started all over again with all the back-up (which must if possible often be recent).
If a stop-gap session on optical press similar to CD plus DVD is closed, this results in being read-only and can simply no lengthier be afflicted with a new trojan (so longer for a virus or perhaps attacked record was not replicated onto this CD/DVD). Likewise, an managing system over a bootable CD may be used to commence the pc if the installed functioning devices grow to be unusable. Backups about detachable press should be carefully inspected prior to restoration. The Gammima virus, to get example, propagates via easily-removed display drives.[22][23]
Another procedure could be to use numerous operating systems about various record systems. A pathogen is just not almost certainly going to influence both. Data backups will also be put on diverse track systems. For example, Linux calls for specific software package in order to produce to NTFS partitions, consequently whenever one will not put in these software program as well as purposes your distinct installation associated with MS Windows in making the backups on a great NTFS partition, your backup need to continue safe through any kind of Linux germs (unless there're published that will specially present this capability). Likewise, MS Windows cannot understand track models for instance ext3, so if one normally employs MS Windows, that backups can certainly be made about an ext3 partition with a Linux installation.
Recovery methods
Once your computer may be compromised by the virus, it is usually harmful to stay when using the same computer without totally reinstalling that operating system. However, you will discover a variety of recovery selections which can be found after a new computer system incorporates a virus. These steps rely on intensity from the form of virus.
Virus removal
One probability about Windows Me, Windows XP in addition to Windows Vista is usually a instrument also known as System Restore, which usually restores this registry as well as critical process information with a previous checkpoint. Often a malware will probably result in a system to help hang, along with a following hard reboot will render a new technique get back point from your identical morning corrupt. Restore details from preceding days need to operate offered herpes is just not made to dodgy the regain documents or perhaps likewise exists with preceding get back points.[24] Some viruses, however, disable system recover and also additional important resources such as Task Manager and Command Prompt. An illustration connected with a malware of which really does that is CiaDoor.
Administrators possess the option for you to disable these applications from restrained users regarding various causes (for example, to cut back likely injury from as well as spread associated with viruses). The trojan changes the registry to be able to do the same, except, should the Administrator is usually controlling the actual computer, them hindrances all end users from getting at the tools. When an afflicted device fires that shows the information "Task Manager has become handicapped by means of ones administrator.", whether or not the user wanting to open up the particular course could be the administrator.[citation needed]
Users managing a Microsoft operating-system can easily accessibility Microsoft's how do people work a free scan, provided they have got their 20-digit subscription number.
Operating program reinstallation
Reinstalling the particular operating-system can be an additional tactic to help virus removal. It involves merely reformatting the actual OS partition as well as adding this OS from it is unique media, or maybe imaging the actual partition which has a clean back up image (Taken with Ghost or Acronis for example).
This technique has the benefits of being basic to do, currently being sooner when compared with running multiple antivirus scans, it is bound to clear away almost any malware. Downsides incorporate requiring you to reinstall most various other software, reconfiguring, rebuilding end user preferences. User info could be copied by booting off of a Live CD or maybe putting that hard drive into an additional laptop in addition to booting through the alternative computer's running process (though proper care have to be consumed certainly not
A computer worm can be a self-replicating computer program. It functions a community to help mail reports of once more in order to various other nodes (computers on the network) but it may perform therefore with virtually no customer intervention. Unlike a virus, them isn't going to need to attach itself for you to a pre-existing program. Worms frequently cause no less than a few damages to your network, only when simply by having bandwidth, while trojans frequently virus ridden or devour files over a targeted computer
Payloads
Many viruses that were made tend to be solely created for you to spread, plus don't try to alter the systems some people move through. However, because Morris earthworm as well as Mydoom showed, your multi-level site visitors along with other unintended side effects can easily generally result in main disruption. A "payload" is rule meant to complete in excess of distribute the actual earthworm - the item may possibly erase data on the coordinator system (e.g., the particular ExploreZip worm), encrypt documents in a very cryptoviral extortion attack, and also send documents via e-mail. A very common payload pertaining to worms is always to install a backdoor within the infected themselves laptop or computer to let your creation of an "zombie" laptop in hand with the earthworm novelist - Sobig in addition to Mydoom are cases which will made zombies. Networks regarding this sort of machines are frequently referred to as botnets and are very commonly used by junk mail senders for mailing crap email in order to cloak the actual